Number of Microsoft competitors has created alternatives to Windows Sidebar. These systems are sometimes designed to be cross-platform—that is, they run on non-Windows systems such as Mac OS X. They also run on previous versions of Windows, such as Windows XP. Most of these products are also free, so while they don’t offer the advantage of shipping inside of Windows, they’re easy enough to obtain online.
All of these environments share the same basic principles, although each has its own differences, advantages, and limitations. The question, of course, is whether any of these alternatives outshine Windows Sidebar enough to consider installing them on Windows Vista.
I’ll state right up front that I don’t think so. Assuming you’re even interested in using gadgets, the way that Sidebar integrates into Windows and is supported by such a wideranging set of third-party gadgets outweighs any small advantages that other environments might have. Installing yet another gadget-type environment would bring little advantage, but would clutter up your desktop in an unnecessary way. Chances are good that if you need a particular kind of gadget, there’s one available for Windows Sidebar, and ultimately that is likely the biggest consideration any potential user should entertain. Yet alternatives do have some advantages. I’ve chosen to focus on two here because they’re both widely used and offer deep integration features with the two most popular online services currently available, Google and Yahoo!. If you’re a heavy user of Google products such as Google Search, Gmail, and Google Calendar, Google Desktop may very much be of interest; and if you’re a big Yahoo! fan, that company’s Yahoo! Widgets provides a compelling Sidebar alternative.
Google Desktop
Google Desktop is Google’s desktop search product, but it has evolved over the years to include far more than just desktop search. Indeed, given the integrated Instant Search functionality that’s now available in Windows Vista, desktop search is barely a reason to even consider Google Desktop anymore. Even Google recognizes this reality: By default,
Google Desktop is no longer preconfigured to index the PC when installed on Windows Vista.
What makes Google Desktop special, in my opinion, are its Google Gadgets and Sidebar features. (Sound familiar?) As with Windows Sidebar, Google Desktop provides a very familiar panel, which can be docked to either side of the screen and can hold several gadgets. It’s just like Windows Sidebar from a usability perspective.
However, because this is Google, the Google Desktop Sidebar comes with a host of Googlemade gadgets that integrate with the many Google online services that are currently available. If you’re a big Google user, as I am, this may put Google Desktop over the top; because while it offers clock, calendar, weather, and notes gadgets just like Windows Sidebar, Google also provides gadgets for Gmail, Google Calendar, Google Video, Google Talk, and other Google services. There are even gadgets for popular non-Google services such as eBay, Twitter, and Wikipedia. Moreover, in my experience, developers have taken to Google’s gadgets much more obviously than they have to those for Windows Sidebar. That suggests that Google Desktop users may have an easier time finding useful new gadgets in the future than Windows Sidebar users.
Google Desktop can be configured to look and function very much like Windows Sidebar. Google Desktop can be downloaded from the Google Web site at http://desktop.google.com/.
Yahoo! Widgets
Give Yahoo! a bit of credit: Not only is its Yahoo! Widgets tool arguably among the first of the desktop gadget tools—it’s based on the Konfabulator engine that has been around for several years—but it also does things its own way. Unlike Google Desktop, Yahoo! Widgets doesn’t look and act almost exactly like Windows Sidebar. Yes, Yahoo! Widgets offers mini-applications, called widgets instead of gadgets, which can live directly on the desktop or be docked on a sidebar-like panel, called a Widget Dock, on the side of the screen. And yes, these widgets often integrate with online services to provide such things as stock quotes, weather, and other timely information.
The similarities end there, however. Yahoo!’s widgets are unique-looking and, dare I say, are generally better-looking than the gadgets offered by Microsoft and Google. For one thing, they’re more consistent: Unlike Microsoft or Google gadgets, Yahoo! widgets are all sized identically when docked, resulting in a cleaner look. (They are different sizes when undocked, or floating on the desktop, however.) You can also choose between available widgets directly from within the Yahoo! Widget Gallery, part of Yahoo! Widgets. That is, you won’t be shuttled off to your Web browser to find other utilities as you are with both Windows Sidebar and Google Desktop.
I also like how Yahoo! handles widget overflow. If you have too many widgets to fit on the dock, you can scroll down the list to access hidden widgets; with Windows Sidebar you have to switch left to right between entire sets of gadgets. Unlike Windows Sidebar, the Yahoo! Widget Dock can be docked to any edge of the screen, not just the left and
right sides. In addition, if you have two monitors, the Dock can extend across both screens if desired.
Yahoo’s product is, of course, linked heavily to Yahoo’s own online services. So if you’re a Yahoo! kind of person, you’ll appreciate integration with Yahoo! services such as Yahoo! Mail, Yahoo! Calendar, Yahoo! Finance, and Flickr. In addition, like Google’s service, Yahoo! Widgets seems to be well supported by developers, and you can find a wide range of third-party widgets out there as well. It’s also available for the Mac, if you’re into that kind of thing.
Yahoo! Widgets is like the quirkier, cooler, younger sibling of Windows Sidebar. Yahoo! Widgets can be downloaded from the Yahoo! Web site at http://widgets.yahoo.com/.
Source of Information : Wiley Windows Vista Secrets SP1 Edition
Advanced Sidebar-Confi guration Options
Although the Sidebar confi guration user interface is fairly complete, there are a few things you can’t easily do. Behind the scenes, however, the Windows Sidebar utilize special confi guration fi les named settings.ini to determine all of its configuration possibilities. If you don’t mind taking a small risk by editing these fi les with a text editor such as Notepad, you can perform various configuration tasks that are impossible with the standard Sidebar UI. Before you make changes, be sure to back up any files you’ll be editing. You’ll also want to quit the Sidebar before editing these files. There are two versions of settings.ini. The first is devoted to system wide configuration options and default settings, and is located in C:\Program Files\Windows Sidebar by default. If you right-click this files and choose Edit, you’ll see the contents of this file, which should resemble the following (obviously, the details vary on a system-by-system basis):
[Root]
SettingsVersion=00.00.00.01
SidebarShowState=Imploded
SidebarDockedPartsOrder=0x1,0x2,0x3,
Section0=1
Section1=2
Section2=3
[Section 1]
PrivateSetting_GadgetName=%PROGRAMFILES%\windows sidebar\gadgets\Clock.
gadget
PrivateSetting_Enabled=true
[Section 2]
PrivateSetting_GadgetName=%PROGRAMFILES%\windows sidebar\gadgets\
SlideShow.Gadget
PrivateSetting_Enabled=true
[Section 3]
PrivateSetting_GadgetName=%PROGRAMFILES%\windows sidebar\gadgets\
RSSFeeds.Gadget
PrivateSetting_Enabled=true
loadFirstTime=defaultGadget
A second version of the Sidebar settings.ini file is available for each user. This file is located in C:\Users\[your user name]\AppData\Local\Microsoft\Windows Sidebar by default. This fi le has a similar structure, but will typically be much longer depending on how much you’ve configured Windows Sidebar. Here’s an example of what the first section of this fi le could look like:
[Root]
SettingsVersion=”00.00.00.01”
SidebarShowState=”Imploded”
SidebarDockedPartsOrder=”0x1,0x2,0x3,0x8,0x5,0x6,0x7,0x9,”
Section0=”1”
SidebarAutoStart=”true”
SidebarDockedPartsPage1=”8”
OneTimeRemoveGadgetMessageShown=”true”
Section1=”2”
Section2=”3”
PickerPosX=”482”
PickerPosY=”313”
Section3=”5”
Section4=”6”
Section5=”7”
Section6=”8”
OneTimeExitMessageShown=”false”
SidebarDockSide=”2”
SidebarAlwaysOnTop=”false”
SidebarDockMonitor=”0”
OneTimeHideMessageShown=”true”
[Section 1]
PrivateSetting_GadgetName=%PROGRAMFILES%\windows sidebar\gadgets\Clock.
gadget
PrivateSetting_Enabled=true
SettingsExist=”True”
clockName=
themeID=”5”
timeZoneIndex=”-1”
secondsEnabled=”False”
PrivateSetting_GadgetTopmost=”false”
PrivateSetting_SidebarDockedState=”Docked”
[Hashes]
...
Take a look at a few of these settings. The SidebarShowState option is set to Imploded in the code example. This means that the Sidebar will be displayed normally, and not in front of other windows. SidebarDockSide is set to 2, which is the right side of the screen. If you change this number to 1, the Windows Sidebar will be displayed on the left. In addition to the options shown here, there are a few other undocumented options. For example, if you’d like a certain gadget to never appear in the Add Gadgets windows, you could simply fi nd the gadget in C:\Program Files\Windows Sidebar\Gadgets and delete it, but what if you wanted it to be available to other users? In this case you could simply add a line like the following to your user’s version of settings.ini:
PickerDefaultPackageSkipList=SlideShow.Gadget,worldClock.Gadget
This particular code would only make the Clock gadget unavailable. Obviously, there are many more settings possibilities. It’s also likely that an enterprising software developer will come up with a TweakUI-style application that provides the same functionality. Stay tuned to my Web site, the SuperSite for Windows, for any breaking news in this regard: www.winsupersite.com.
Source of Information : Wiley Windows Vista Secrets SP1 Edition
[Root]
SettingsVersion=00.00.00.01
SidebarShowState=Imploded
SidebarDockedPartsOrder=0x1,0x2,0x3,
Section0=1
Section1=2
Section2=3
[Section 1]
PrivateSetting_GadgetName=%PROGRAMFILES%\windows sidebar\gadgets\Clock.
gadget
PrivateSetting_Enabled=true
[Section 2]
PrivateSetting_GadgetName=%PROGRAMFILES%\windows sidebar\gadgets\
SlideShow.Gadget
PrivateSetting_Enabled=true
[Section 3]
PrivateSetting_GadgetName=%PROGRAMFILES%\windows sidebar\gadgets\
RSSFeeds.Gadget
PrivateSetting_Enabled=true
loadFirstTime=defaultGadget
A second version of the Sidebar settings.ini file is available for each user. This file is located in C:\Users\[your user name]\AppData\Local\Microsoft\Windows Sidebar by default. This fi le has a similar structure, but will typically be much longer depending on how much you’ve configured Windows Sidebar. Here’s an example of what the first section of this fi le could look like:
[Root]
SettingsVersion=”00.00.00.01”
SidebarShowState=”Imploded”
SidebarDockedPartsOrder=”0x1,0x2,0x3,0x8,0x5,0x6,0x7,0x9,”
Section0=”1”
SidebarAutoStart=”true”
SidebarDockedPartsPage1=”8”
OneTimeRemoveGadgetMessageShown=”true”
Section1=”2”
Section2=”3”
PickerPosX=”482”
PickerPosY=”313”
Section3=”5”
Section4=”6”
Section5=”7”
Section6=”8”
OneTimeExitMessageShown=”false”
SidebarDockSide=”2”
SidebarAlwaysOnTop=”false”
SidebarDockMonitor=”0”
OneTimeHideMessageShown=”true”
[Section 1]
PrivateSetting_GadgetName=%PROGRAMFILES%\windows sidebar\gadgets\Clock.
gadget
PrivateSetting_Enabled=true
SettingsExist=”True”
clockName=
themeID=”5”
timeZoneIndex=”-1”
secondsEnabled=”False”
PrivateSetting_GadgetTopmost=”false”
PrivateSetting_SidebarDockedState=”Docked”
[Hashes]
...
Take a look at a few of these settings. The SidebarShowState option is set to Imploded in the code example. This means that the Sidebar will be displayed normally, and not in front of other windows. SidebarDockSide is set to 2, which is the right side of the screen. If you change this number to 1, the Windows Sidebar will be displayed on the left. In addition to the options shown here, there are a few other undocumented options. For example, if you’d like a certain gadget to never appear in the Add Gadgets windows, you could simply fi nd the gadget in C:\Program Files\Windows Sidebar\Gadgets and delete it, but what if you wanted it to be available to other users? In this case you could simply add a line like the following to your user’s version of settings.ini:
PickerDefaultPackageSkipList=SlideShow.Gadget,worldClock.Gadget
This particular code would only make the Clock gadget unavailable. Obviously, there are many more settings possibilities. It’s also likely that an enterprising software developer will come up with a TweakUI-style application that provides the same functionality. Stay tuned to my Web site, the SuperSite for Windows, for any breaking news in this regard: www.winsupersite.com.
Source of Information : Wiley Windows Vista Secrets SP1 Edition
What Is Windows Sidebar?
Back when Microsoft shipped Windows 98, it added a debatably useful feature called Active Desktop that provided an HTML (Hypertext Markup Language) layer on top of the traditional desktop. Active Desktop was an attempt to capitalize on the then-emerging trend of users wanting to combine live data from the Web with their PC operating system.
The term for this at the time was push technology. The idea was that although you could use a Web browser to manually find data on the Web, or pull data from the Web, a pushtechnology client like Active Desktop could push data to the user automatically with no interaction required.
Ultimately, users found Active Desktop to be confusing and undesirable, mostly because
Microsoft and its partners used it as a front end for advertisements and other unwanted information; and although the feature was never really removed from Windows, it was deemphasized in subsequent Windows versions, such as Windows XP. However, it’s still possible to add Web content to your XP desktop via Active
Desktop if you really want to.
Active Desktop may have failed, but the underlying benefits of push technology are still valid today. You can see that this type of functionality still exists in such technologies as RSS (Really Simple Syndication), which in fact attempts to solve essentially the same problem as Active Desktop: Rather than force users to manually search for the content they want, that content is delivered automatically to them using a unique kind of client
(in this case, an RSS client).
In Windows Vista, Active Desktop is finally gone forever, but integrated push technology lives on with a brand-new feature called Windows Sidebar. Like Active Desktop,
Windows Sidebar is available by default and is running when you start up your new Windows Vista–based PC for the first time. Moreover, it will keep on running unless you configure it not to do so, but Windows Sidebar solves one of Active Desktop’s major problems by moving the main user interface off the desktop and to the side of the screen where it won’t typically be hidden under your open applications and other windows. (If it is hidden by windows, you can optionally configure Windows Sidebar to appear “on top” of other windows.)
Source of Information : Wiley Windows Vista Secrets SP1 Edition
The term for this at the time was push technology. The idea was that although you could use a Web browser to manually find data on the Web, or pull data from the Web, a pushtechnology client like Active Desktop could push data to the user automatically with no interaction required.
Ultimately, users found Active Desktop to be confusing and undesirable, mostly because
Microsoft and its partners used it as a front end for advertisements and other unwanted information; and although the feature was never really removed from Windows, it was deemphasized in subsequent Windows versions, such as Windows XP. However, it’s still possible to add Web content to your XP desktop via Active
Desktop if you really want to.
Active Desktop may have failed, but the underlying benefits of push technology are still valid today. You can see that this type of functionality still exists in such technologies as RSS (Really Simple Syndication), which in fact attempts to solve essentially the same problem as Active Desktop: Rather than force users to manually search for the content they want, that content is delivered automatically to them using a unique kind of client
(in this case, an RSS client).
In Windows Vista, Active Desktop is finally gone forever, but integrated push technology lives on with a brand-new feature called Windows Sidebar. Like Active Desktop,
Windows Sidebar is available by default and is running when you start up your new Windows Vista–based PC for the first time. Moreover, it will keep on running unless you configure it not to do so, but Windows Sidebar solves one of Active Desktop’s major problems by moving the main user interface off the desktop and to the side of the screen where it won’t typically be hidden under your open applications and other windows. (If it is hidden by windows, you can optionally configure Windows Sidebar to appear “on top” of other windows.)
Source of Information : Wiley Windows Vista Secrets SP1 Edition
Adobe Online Tools for Documents and Presentations
ADOBE'S ACROBAT.COM has free content-creation tools that can help in a pinch or even be a regular part of your workday. Most of the Webbased applications are collaborative, and Adobe will even host your files, so both the app and the documents can be accessed on any Pc. It's great if you bounce between machines and don't carry a USB drive. Adobe Buzzword is a word processor, and Adobe ConnectNow handles online meetings. Just released is a presentation tool, called simply Presentations. Most of the tools require Flash 9; Presentations needs Flash 10. Set up a free account, log in, and work away. With Buzzword, you can adjust fonts, formatting, and other text basics, as well as insert images. It's also great for collaboration. As with Google Docs, you invite contacts to view or edit a file, and you can make changes at the same time. A commenting tool lets you 3dd notations.
Buzzword imports and exports Word, Open Doc, t ext, and RTF files; it also exports as PDF, HTML, or .epub (Adobe'S e-reader format). In Connct:tNow online meetings, up to three people can share desktops and documents using the live screen casting tool. Its VolP option handles spoken conversations-a chat window works for typing-and 3 collaborative whiteboard allows everyone to focus on the same thing. A presentation is hosted at labs.acrobat.com because it has additional critical features coming. For example, it can't yet export PowerPoint files-a deal-breaker for many small businesses. But Adobe is working on adding that option, which may come by the end of this year.
Overall, Presentations follows the familiar slide-creation paradigm of PowerPoint. Unlike in that Office app, you can invite an unlimited number of people to view or edit the files, making Presentations 3 hub for both collaboration and showing slides.
Buzzword imports and exports Word, Open Doc, t ext, and RTF files; it also exports as PDF, HTML, or .epub (Adobe'S e-reader format). In Connct:tNow online meetings, up to three people can share desktops and documents using the live screen casting tool. Its VolP option handles spoken conversations-a chat window works for typing-and 3 collaborative whiteboard allows everyone to focus on the same thing. A presentation is hosted at labs.acrobat.com because it has additional critical features coming. For example, it can't yet export PowerPoint files-a deal-breaker for many small businesses. But Adobe is working on adding that option, which may come by the end of this year.
Overall, Presentations follows the familiar slide-creation paradigm of PowerPoint. Unlike in that Office app, you can invite an unlimited number of people to view or edit the files, making Presentations 3 hub for both collaboration and showing slides.
Portable Hotspot Is a Hot Product for Business
THE NOVATEL MIFI personal hotspot device from Verizon Wireless (find pcworld.com/63217) is an idea so good that I'm shocked it's just now coming to market. And for once, the price is right. Carry-around connectivity has taken a great leap forward. The MiFi is a tiny (3.5 by 2.3 by 0.4 inches) Linux-based Wi-Fi router that weighs about 2 ounces. Unlike the wireless data cards that cellular providers offer, the MiFi Jets up to five computers or other wireless devices share a single broadband connection on the Verizon EvDO network. Theoretical download speed is 3.1 megabits per second, and is shared among all devices connected to the MiFi. (Your download speed is more likely to be in the I-mbps range.)
Verizon charges $270 for the device and $15 per day for unlimited use. That's a good deal for multi device, broadband connectivity where a normal Wi-Fi hotspot is not available. Because the MiFi is something I would use only occasionally, for moving a fair amount of data over multiple PCs, that pricing works best for me.
Other pricing plans cost $100 for the hardware (after a $50 mail-in rebat) and about $60 per month for 5GB of data or $40 per month for 250MB. The MiFi can run for 4 hours on 3 charge. Though that's longer than many laptops manage, it doubtless represents a size/weight compromise on the part of the MiFi's designers. Businesses will flock to this device, which should be on s3Je now. It will no longer matter if no public Wi-Fi is available when you want to connect more than one computer to the Internet. One potemi3J drawback might be Wi-Fi interference at gatherings where people show up with a number of MiFi units. Also, bandwidth must be shared among all users of a cellular tower. -DaoidConry
Source of Information : PC World August 2009
Kexi
Kexi, part of the KOffice suite, allows anyone to create, populate, and maintain a database.
The open source world offers a number of solutions for managing data. SQLite is a tiny yet powerful database; MySQL is extremely popular with web developers; and PostgreSQL boasts transactional features on par with Oracle. All three solutions have command line and programmatic interfaces, and both MySQL and PostgreSQL have support for browser-based management. SQLite, MySQL, and PostgreSQL all have strengths and weaknesses, and each is capable, but sadly, none of the three is suitable for the new Linux netbook owner or casual desktop user. Indeed, Linux users have had few options for a friendly, graphical, and lightweight database solution akin to Microsoft Access.
A Windows user can build tables, enter data, formulate queries, and craft reports in Access with little more than a mouse. The OpenOffice.org Base tool attempts a similar mission within Linux environments, but some popular distros don't include Base with the default desktop, and many Linux users are still searching for other options.
The Kexi database development tool is another alternative for many Linux users. Kexi, billed as “Access for Linux,” has been available since 2006, and the latest stable release, Kexi 1.1.3, is part of the KOffice 1.6 suite. Kexi 1.1.3, which I used for this article, dates to April 2008, but Kexi 2.0 is marching through a series of pre-releases, with the intention to ship by the end of the year.
Introducing Kexi
Kexi, like Microsoft Access, offers a friendly user interface to create, populate, and maintain a database. Many tasks in Kexi are like filling out a spreadsheet. For example, to create a table, you fill out a row for each field in the table. Then you name each field, assign a type (such as date, integer, or text), and perhaps link the new field to an existing field in another table, thereby relating the two tables (hence the name “relational database”). Once you define a table, you can populate it with data as you would a spreadsheet.
Crafting queries in Kexi is a little more involved but does not require any knowledge of SQL. Instead, a query is largely drag and drop: Choose one or more tables, relate one field to another by point and click, and select the fields you want to display. Kexi also offers drag-and-drop form building to create interfaces to enter data, and like Access, Kexi either can use its own database format or can connect to another engine for more oomph. In Kexi’s case, you can use MySQL. If you dislike the phpMyAdmin interface, try Kexi to browse an existing MySQL database.
Kexi is modal. The Design View creates and edits tables, queries, and forms, whereas the Data View shows the end result. Building an application in Kexi is typified by switching from one mode to the other. First I’ll use Kexi to build an application, exploring its features along the way.
Installing Kexi
The easiest and fastest way to install Kexi is via your package manager. On Debian and Ubuntu variants, use apt-get or one of the equivalent graphical front ends:
$ sudo apt-get update
$ sudo apt-get install kexi
Kexi depends on KDE [5]. If you do not use KDE or any of its components, the addition of Kexi, KDE, and the latter package’s attendant dependencies could add some 100 packages to your system, including the KOffice suite. Otherwise, the process is very quick. After the installation finishes, run Kexi:
$ kexi
When the Choose Project window pops up, choose Blank Database and click OK. The next prompt asks where you would like to create the database. The two choices are in a file or in a MySQL database server. To keep things simple, choose New Project Stored in File. When Kexi asks for a database name, enter Example One, click OK, and use the browse dialog to choose a location for the file on your disk.
The pane on the left collects your tables, queries, forms, and scripts (the latter is an experimental feature and is ignored here). Kexi calls each of those entities an object. To create a new table, for example, rightclick on Tables and choose Create Object: Table. (From the menubar: Choose Insert| Table.) The tool palette is immediately below the menubar; the list of available tools changes depending on the task at hand. The central area of the Kexi window is the heart of the application, in that most of your work is performed here. The rightmost panel, which is empty in but shown in subsequent figures, is used to edit the attributes of fields.
Source of Information : Linux Pro Magazine August 2009
The open source world offers a number of solutions for managing data. SQLite is a tiny yet powerful database; MySQL is extremely popular with web developers; and PostgreSQL boasts transactional features on par with Oracle. All three solutions have command line and programmatic interfaces, and both MySQL and PostgreSQL have support for browser-based management. SQLite, MySQL, and PostgreSQL all have strengths and weaknesses, and each is capable, but sadly, none of the three is suitable for the new Linux netbook owner or casual desktop user. Indeed, Linux users have had few options for a friendly, graphical, and lightweight database solution akin to Microsoft Access.
A Windows user can build tables, enter data, formulate queries, and craft reports in Access with little more than a mouse. The OpenOffice.org Base tool attempts a similar mission within Linux environments, but some popular distros don't include Base with the default desktop, and many Linux users are still searching for other options.
The Kexi database development tool is another alternative for many Linux users. Kexi, billed as “Access for Linux,” has been available since 2006, and the latest stable release, Kexi 1.1.3, is part of the KOffice 1.6 suite. Kexi 1.1.3, which I used for this article, dates to April 2008, but Kexi 2.0 is marching through a series of pre-releases, with the intention to ship by the end of the year.
Introducing Kexi
Kexi, like Microsoft Access, offers a friendly user interface to create, populate, and maintain a database. Many tasks in Kexi are like filling out a spreadsheet. For example, to create a table, you fill out a row for each field in the table. Then you name each field, assign a type (such as date, integer, or text), and perhaps link the new field to an existing field in another table, thereby relating the two tables (hence the name “relational database”). Once you define a table, you can populate it with data as you would a spreadsheet.
Crafting queries in Kexi is a little more involved but does not require any knowledge of SQL. Instead, a query is largely drag and drop: Choose one or more tables, relate one field to another by point and click, and select the fields you want to display. Kexi also offers drag-and-drop form building to create interfaces to enter data, and like Access, Kexi either can use its own database format or can connect to another engine for more oomph. In Kexi’s case, you can use MySQL. If you dislike the phpMyAdmin interface, try Kexi to browse an existing MySQL database.
Kexi is modal. The Design View creates and edits tables, queries, and forms, whereas the Data View shows the end result. Building an application in Kexi is typified by switching from one mode to the other. First I’ll use Kexi to build an application, exploring its features along the way.
Installing Kexi
The easiest and fastest way to install Kexi is via your package manager. On Debian and Ubuntu variants, use apt-get or one of the equivalent graphical front ends:
$ sudo apt-get update
$ sudo apt-get install kexi
Kexi depends on KDE [5]. If you do not use KDE or any of its components, the addition of Kexi, KDE, and the latter package’s attendant dependencies could add some 100 packages to your system, including the KOffice suite. Otherwise, the process is very quick. After the installation finishes, run Kexi:
$ kexi
When the Choose Project window pops up, choose Blank Database and click OK. The next prompt asks where you would like to create the database. The two choices are in a file or in a MySQL database server. To keep things simple, choose New Project Stored in File. When Kexi asks for a database name, enter Example One, click OK, and use the browse dialog to choose a location for the file on your disk.
The pane on the left collects your tables, queries, forms, and scripts (the latter is an experimental feature and is ignored here). Kexi calls each of those entities an object. To create a new table, for example, rightclick on Tables and choose Create Object: Table. (From the menubar: Choose Insert| Table.) The tool palette is immediately below the menubar; the list of available tools changes depending on the task at hand. The central area of the Kexi window is the heart of the application, in that most of your work is performed here. The rightmost panel, which is empty in but shown in subsequent figures, is used to edit the attributes of fields.
Source of Information : Linux Pro Magazine August 2009
Five Simple, Free Security Hacks
Security software is the lock on your PC’s front door, but you can also make that door less attractive to crooks.
Let’s talk about security hacks— simple yet clever ways to protect yourself and your PC that cost little or nothing. Here are my five favorites. It should go without saying that none of these can replace good, up-to-date antivirus and firewall protection, but they can make stealing your system or data difficult or unappealing.
1. It’s simple, yet surprisingly effective: Remove the keyboard and mouse. It’s highly unlikely that a snoop will carry an extra keyboard and mouse with him. This will slow someone down but is far from foolproof, and it should go without saying that every computer should be physically locked to a sturdy object and secured behind a strong password.
2. To protect from podslurping (the connecting of an unauthorized USB device and its use to steal data), disable your USB ports. Or—and we borrowed this one directly from the U.S. military— epoxy over the USB ports. Too permanent? A slightly more elegant solution is to open the PC case and disconnect (or cut) the wires running from the motherboard to the USB ports.
3. Traveling with a laptop? Try not to advertise that you’re carrying a valuable piece of equipment: Use a computer bag that doesn’t look like a computer bag, or use a neoprene sleeve inside a regular backpack. If you nap at the airport, wrap the shoulder strap around your arm or leg so you’ll be alerted if someone tries to walk away with your bag.
4. Here’s an easy way to hide your Windows PC on a network while maintaining access to network resources. (This also works when you want stealth but still want to let others access your shared resources.) At the command prompt, type
Net config server /hidden:yes
Now you’re still a member of your network neighborhood, but your PC won’t show up when others browse for it. Make sure your software firewall is turned on, and block incoming ICMP traffic. This will prevent a network intruder from scanning for your PC using a ping sweep. Once you are hidden on the network, you can spend some time trying to figure out who, if anyone, is connecting to your PC and to whom your PC is connecting. To accomplish this, you’ll use the command-line tool Netstat and the Task Manager. Get to the command prompt and type
netstat –ao
A bunch of info will flash by on your screen listing the type of connection, the IP addresses of remote hosts, the protocols, and the process identifier, or PID. If there’s something here you don’t recognize, write down the PID. Now, open the Task Manager and add the PID column by opening the View menu and clicking on Select Columns. Check the box next to PID. Now match the PID from Netstat and the PID from Task Manager to learn which applications are holding which ports open. A well-secured machine should have ports open only for authorized apps.
5. One last idea: Enabling secure logon in Windows XP and Vista will protect your system from malware that attempts to impersonate a log-on screen to steal system passwords. This forces anyone trying to log on to press Ctrl-Alt-Del first. In Windows Vista, open the Run command, type netplwiz, and click Continue when prompted by User Account Control. In the Advanced User Account window, click the Advanced tab, then select the box that says Require users to press Ctrl-Alt-Delete. In Windows XP, go to the Control Panel’s User Accounts applet. In the Advanced User Account window, click the Advanced tab, then select the box that says Require users to press Ctrl-Alt-Delete.
Source of Information : PC Magazine July 2009
Let’s talk about security hacks— simple yet clever ways to protect yourself and your PC that cost little or nothing. Here are my five favorites. It should go without saying that none of these can replace good, up-to-date antivirus and firewall protection, but they can make stealing your system or data difficult or unappealing.
1. It’s simple, yet surprisingly effective: Remove the keyboard and mouse. It’s highly unlikely that a snoop will carry an extra keyboard and mouse with him. This will slow someone down but is far from foolproof, and it should go without saying that every computer should be physically locked to a sturdy object and secured behind a strong password.
2. To protect from podslurping (the connecting of an unauthorized USB device and its use to steal data), disable your USB ports. Or—and we borrowed this one directly from the U.S. military— epoxy over the USB ports. Too permanent? A slightly more elegant solution is to open the PC case and disconnect (or cut) the wires running from the motherboard to the USB ports.
3. Traveling with a laptop? Try not to advertise that you’re carrying a valuable piece of equipment: Use a computer bag that doesn’t look like a computer bag, or use a neoprene sleeve inside a regular backpack. If you nap at the airport, wrap the shoulder strap around your arm or leg so you’ll be alerted if someone tries to walk away with your bag.
4. Here’s an easy way to hide your Windows PC on a network while maintaining access to network resources. (This also works when you want stealth but still want to let others access your shared resources.) At the command prompt, type
Net config server /hidden:yes
Now you’re still a member of your network neighborhood, but your PC won’t show up when others browse for it. Make sure your software firewall is turned on, and block incoming ICMP traffic. This will prevent a network intruder from scanning for your PC using a ping sweep. Once you are hidden on the network, you can spend some time trying to figure out who, if anyone, is connecting to your PC and to whom your PC is connecting. To accomplish this, you’ll use the command-line tool Netstat and the Task Manager. Get to the command prompt and type
netstat –ao
A bunch of info will flash by on your screen listing the type of connection, the IP addresses of remote hosts, the protocols, and the process identifier, or PID. If there’s something here you don’t recognize, write down the PID. Now, open the Task Manager and add the PID column by opening the View menu and clicking on Select Columns. Check the box next to PID. Now match the PID from Netstat and the PID from Task Manager to learn which applications are holding which ports open. A well-secured machine should have ports open only for authorized apps.
5. One last idea: Enabling secure logon in Windows XP and Vista will protect your system from malware that attempts to impersonate a log-on screen to steal system passwords. This forces anyone trying to log on to press Ctrl-Alt-Del first. In Windows Vista, open the Run command, type netplwiz, and click Continue when prompted by User Account Control. In the Advanced User Account window, click the Advanced tab, then select the box that says Require users to press Ctrl-Alt-Delete. In Windows XP, go to the Control Panel’s User Accounts applet. In the Advanced User Account window, click the Advanced tab, then select the box that says Require users to press Ctrl-Alt-Delete.
Source of Information : PC Magazine July 2009
How to Install the Windows 7 Release Candidate
 With a smaller footprint, better performance, multitouch support, and even some eye candy, the Release Candidate of Windows 7 is garnering tons of praise. In my hands-on analysis of the OS (also referred to as build number 7100), I wrote “Quicker to install, more polished and customizable, and easier to use than earlier builds, the Windows 7 Release Candidate (build 7100) is a nice step towards finalization of the operating system.” But enough talk. You’re ready and eager to give it a try yourself. So how to get started? Let me walk you through the decisions you need to make before installing the new operating system, and the steps you need to take to ensure a seamless, troublefree experience.
With a smaller footprint, better performance, multitouch support, and even some eye candy, the Release Candidate of Windows 7 is garnering tons of praise. In my hands-on analysis of the OS (also referred to as build number 7100), I wrote “Quicker to install, more polished and customizable, and easier to use than earlier builds, the Windows 7 Release Candidate (build 7100) is a nice step towards finalization of the operating system.” But enough talk. You’re ready and eager to give it a try yourself. So how to get started? Let me walk you through the decisions you need to make before installing the new operating system, and the steps you need to take to ensure a seamless, troublefree experience. INSTALL THE UPGRADE ADVISOR BETA Once
INSTALL THE UPGRADE ADVISOR BETA Onceyou’ve figured out where you’re going to install
the OS, this is your next step. The Upgrade
Advisor will make sure there are no compatibility
issues or any other potential problems with
your hardware.
Step 1: Make a Plan
Before all else, make sure you know where you’ll be installing the OS and how you plan to do so. There are three common scenarios: Installing fresh on an older PC, partitioning your hard drive and setting up dual booting, or upgrading a Vista (or earlier Win7 beta) partition. Do you have an older PC that you want to play around with? Or will you be making space on your current PC? Let’s look at each scenario.
CLEAN INSTALLATION If you’ve got an older system, it’s probably running Windows XP, and you’re probably planning on erasing that system and starting from scratch. Good plan. A clean install is the most trouble-free option and should cause you the fewest problems.
UPGRADE You can’t upgrade an XP installation, only a PC running Windows Vista. And you can’t upgrade an existing Windows partition if you boot from the Windows 7 disc. Instead, you’ll boot and run the Windows disc from within your current partition, following the instructions in the autorun app.
PARTITION To enable the partitioning features built into the Windows 7 Release Candidate installer, you need to boot from the disc. But be forewarned: You can’t simply shrink your current partition using the tool (although you can partition from within Windows Vista). The Windows 7 partition tool is really designed to work with raw disk space, meaning it will let you delete and recreate partitions, not resize existing ones. Alternatively, you can use third-party software to resize a partition; I like Paragon Partition Manager, but there are several options available. Stop to think about your time frame here as well. The Windows 7 Release Candidate will stop running on June 1, 2010, at which point you’re going to be forced to buy the darn thing. But don’t worry about writing that date down: Microsoft warns that “starting on March 1, 2010, your PC will begin shutting down every 2 hours. Windows will notify you two weeks before the bi-hourly shutdowns start. To avoid interruption, you’ll need to install a non-expired version of Windows before March 1, 2010.” Some people would label this “annoyingware.” But can you really fault the company for giving you a full year of free usage?
 PREPARE TO RUN THE
PREPARE TO RUN THEUPGRADE ADVISOR The
Upgrade Advisor will make
sure your CPU, RAM, hard
drive, and graphics card all
meet the minimum system
specs.
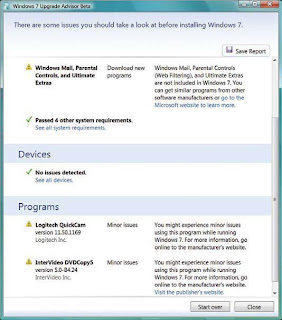 WINDOWS UPGRADE ADVISOR RESULTS The
WINDOWS UPGRADE ADVISOR RESULTS TheUpgrade Advisor’s useful “Programs” section
lets you know of any potential software problems.
You might want to consider replacing
software listed here to make sure Windows 7
runs smoothly.
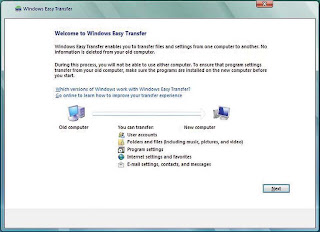 RUN THE EASY TRANSFER
RUN THE EASY TRANSFERUTILITy This utility allows you
to move your files and settings
from an old PC to an external
hard drive, a network drive, or
a USB flash drive.
Step 2: Prepare
Now, download and run the Windows 7 Upgrade Advisor Beta: It will check your hardware to ensure compatibility and let you know about any potential problems you may encounter. You’ll have to accept a User Account Control prompt before installing (and running) the tool, of course; the Upgrade Advisor will suggest a path to Windows 7, be it an upgrade or a clean install, and will test your CPU, RAM, hard drive, and graphics card to make sure they meet the minimum system specs: I’m an enthusiast—and my PCs are backed up several ways—so I have no problem installing beta software. Even so, I’m leery of installing an unfinished operating system on my main PC; you should be as well. For this reason, you’ll probably find the Upgrade Advisor’s section on “Programs” the most useful to you. Here’s where you can see anything that may present problems for you; in my case, the suspect programs were Logitech’s QuickCam software and an outdated copy of Corel’s DVDCopy. If you see anything crucial, now’s the time to think about replacing the software or figuring out some way to make it work. If you’re upgrading from Windows Vista or installing onto an older PC that you don’t use often, I suggest you try out the Windows Easy Transfer Utility. It lets you migrate your files and system and app settings from that old PC to an external hard drive, network drive, or USB flash drive. Later on you can port all that data and customization back onto your new Windows 7 system. You can search for the Easy Transfer Utility on Vista’s Start menu, or in XP find it under Accessories | System Tools. The utility is pretty simple to muddle through, but for detailed directions, follow along with the step-by-step instructions on Microsoft TechNet.
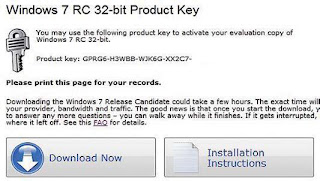 DOWNLOAD THE RELEASE CANDIDATE
DOWNLOAD THE RELEASE CANDIDATEOnce you’ve entered a Windows Live ID or
signed up for one, Microsoft will generate a new
key, which will activate Windows 7 on up to
three PCs.
Step 3. Download and burn
You can download the Release Candidate and get your own product key through July. To do so, head over to Microsoft’s Windows 7 download page. Follow the download links and enter a Windows Live ID (or sign up for one); the site will generate a new key especially for you. The key will activate Windows 7 on up to three PCs. I’ve knocked the last five characters off my key in the screenshot— you’ll have to get your own! And for once, Microsoft hasn’t restricted the download site to IE users only; users of Firefox can get there as well. The RC is a giant file, of course; the 32-bit version is called “7100.0.090421-1700_x86fre_client_en-us_retail_ultimategrc1culfrer_en_dvd.iso,” and it’s 2.36GB. So to download it, Microsoft uses a Java-based download manager from Akamai Technologies. This is handy, because it means that if the download is interrupted, you’ll find a “Start Download Manager.html” icon on your desktop. You can click it to restart the download, and it will pick up where it left off. Once you’ve downloaded the file, which comes as a disc image called an ISO, you’ll need to turn it into a DVD. I’m a fan of Img-Burn, a lightweight, easy-to-use tool for turning disc images into actual discs. It’s fairly self-explanatory software that should be part of everyone’s standard utility toolkit. When you’ve finished burning the disc, fire up your PC and run the installer. Alternatively, you can copy the files to a USB thumb drive and install the OS from there. This lets you circumvent the whole “burn a DVD” stage, and in theory, the installation from flash memory should be slightly quicker than installation from an optical disc. But in our experience, the process is more complicated than necessary. After all, DVDs are quite inexpensive. Instead, burn a disc with the ISO file and copy the Windows 7 RC to your thumb drive straight off the optical media: It will have all the files necessary to let you boot from the flash drive and will work just as smoothly as a DVD.
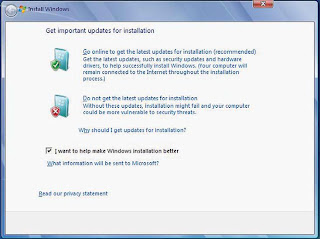 GET IMPORTANT UPDATES
GET IMPORTANT UPDATESThe installer will ask whether
you want to go online to
download any updates. It will
then actually find the updates
for you and download them.
Step 4: Installation
The Windows 7 Release Candidate is designed to install the Ultimate edition of the operating system, even though Microsoft will probably release as many versions of Win7 as there were of Windows Vista. If you’d like, you can “unlock” the other versions of the operating system, which are hidden on the ISO you just downloaded. ZDNet’s Ed Bott points out that to do so, you simply open the Sources folder, find the file Ei.cfg, and delete it. Once you’ve fired up the installer, it will ask whether you’d like to go online to download any updates, and then it will go and actually find the updates you need—what a shock! Vista asks the same question—as did XP, if memory serves—but it never actually seems to download anything. Accept the license agreement and you are ready to rock. The installer will reboot once or twice, and then it will ask you for information about your network, but the process is more or less unattended. Once you’ve finished, you’re free to configure your desktop, set up your libraries, play songs anywhere with Play To, pin apps and documents to your jumplists, and explore all the other cool new features.
Source of Information : PC Magazine July 2009
Windows Server 2008 R2
Windows Server 2008 R2 Free with Windows Server 2008 license; new R2 license pricing not yet announced.
PROS : Huge enhancements in Hyper-V. New document management abilities in file services. Supports live migration of virtual servers.
CONS : Making Clustering, Hyper-V, and DirectAccess could require advanced IT expertise.
A Significant Server OS Release Typically, R2 server announcements represent the midpoint between major releases and thus are not very exciting. But this time, Microsoft has revealed several new features and big improvements in its release, including vastly improved Hyper-V support, an integrated documentmanagement system, the beginning of the end of the hated VPN, and much more granular backup support. These new features signal an aggressive move by Microsoft to entice companies of all sizes, and especially SMBs, to make the switch to Server 2008. In R2, Microsoft has ramped up its Hyper-V virtualization to perform live migration so you can move virtual servers that are running in Hyper-V among multiple physical servers without dropping network connections or requiring any downtime. R2 now supports up to 256 logical processor cores and has enhanced its access to non-uniform memory access (NUMA) hardware, making it about 30 percent faster than the original release of Server 2008. There is also File Classification Infrastructure (FCI) document management technology, which can change the location of files or even delete them based on a classification that you define. R2 has replaced its VPN with DirectAccess (but only in a Windows 7 environment). And the backup feature has been enhanced to include individual files and folders, instead of only entire volumes (though there’s still room for improvement here). All this adds up to an R2 release that’s far from dull. In fact, it’s an Editors’ Choice.—Mario Morejon
Source of Information : PC Magazine July 2009
PROS : Huge enhancements in Hyper-V. New document management abilities in file services. Supports live migration of virtual servers.
CONS : Making Clustering, Hyper-V, and DirectAccess could require advanced IT expertise.
A Significant Server OS Release Typically, R2 server announcements represent the midpoint between major releases and thus are not very exciting. But this time, Microsoft has revealed several new features and big improvements in its release, including vastly improved Hyper-V support, an integrated documentmanagement system, the beginning of the end of the hated VPN, and much more granular backup support. These new features signal an aggressive move by Microsoft to entice companies of all sizes, and especially SMBs, to make the switch to Server 2008. In R2, Microsoft has ramped up its Hyper-V virtualization to perform live migration so you can move virtual servers that are running in Hyper-V among multiple physical servers without dropping network connections or requiring any downtime. R2 now supports up to 256 logical processor cores and has enhanced its access to non-uniform memory access (NUMA) hardware, making it about 30 percent faster than the original release of Server 2008. There is also File Classification Infrastructure (FCI) document management technology, which can change the location of files or even delete them based on a classification that you define. R2 has replaced its VPN with DirectAccess (but only in a Windows 7 environment). And the backup feature has been enhanced to include individual files and folders, instead of only entire volumes (though there’s still room for improvement here). All this adds up to an R2 release that’s far from dull. In fact, it’s an Editors’ Choice.—Mario Morejon
Source of Information : PC Magazine July 2009
Acer Aspire 3935

Acer’s Budget Laptop Home Run
Acer has been delivering affordable systems for as long as the company has existed. The majority of those systems, however, have come with design trade-offs. Often they were too thick, too heavy, or just plain ugly. The Aspire 3935 ushers in what we hope will be a new era for the company. The sleek metallic cover, the 1-inchthick chassis, and the sheer portability of this system are qualities that customers have been yearning for but hadn’t been able to get in such a sweet deal. The 3935 is a huge departure from Acer systems like the Aspire 6930G and the Aspire One (10-inch) in that the thick plastic cases have been replaced by brushed aluminium on the lid. The 3935 is almost as thin as the Apple MacBook 13-inch (Aluminum) and weighs just 4.1 pounds. The 13.3-inch widescreen is work- and media-friendly, and the small touchpad has multitouch features, though they were somewhat unresponsive. Arguably the most desirable feature on the 3935 is the built-in dual-layer DVD burner. The most glaring omission: an HDMI-out port. The 3935 is also GreenTech Approved, for meeting our criteria on materials, energy efficiency, and recyclability. The 3935’s most impressive performance feat was its battery life. Most of its competitors have bigger batteries but can’t achieve the 3935’s 4-hour 50-minute battery score. It says a lot when a company can produce a gorgeous design at a price many would call a bargain. The metallic design and surprisingly good battery score alone are worthy of an Editors’ Choice; we consider the speedy components, ample features, and GreenTech seal extra credit.—Cisco Cheng

Source of Information : PC Magazine July 2009
The Bottomless DVD

A new breakthrough could herald the 10-terabyte disc.
What is store in the five-dimensional storage system developed by an Australian research team takes traditional 2D storage and adds multiple layers, color coding, and polarization of the light. The storage medium is a network of gold nanorods.
Imagine storing 10,000 standard-definition movies on one disc. Sound impossible? Not to a team of Australian researchers. The team recently published a report in the journal Nature in which it details its development of a “five-dimensional” storage medium that promises to store up 10 terabytes on a single disc. Peter Zijlstra, James W.M. Chon, and Min Gu of the Swinburne University of Technology found a way to combine addressing data using wavelength, polarization, and three spatial dimensions, creating the so-called five dimensions of addressable space. The approach allows for a storage density of a terabit of information in just a cubic centimeter of space.
Mixing and matching different methods of addressing data has been tried using individual methods, the researchers said. In fact, writing data to a three-dimensional storage medium has been one of the hallmarks of holographic storage. But for fivedimensional storage, the team projected information into the material using different color wavelengths. Additional information was then added by polarizing the light, first at a fixed orientation and then by rotating the filter 90 degrees. Data was read using a technique called “longitudinal SPRmediated 2-photon luminescence.”
It’s difficult to say, however, how easily a solution like this might be moved into production, since the medium used to store the information is a network of gold nanorods. “The major hurdle is the lack of a suitable recording medium that is extremely selective in the domains of wavelength and polarization,” the researchers wrote in an abstract. Nonetheless, companies such as Samsung have already expressed interest. —Mark Hachman
Source of Information : PC Magazine July 2009
NetBIOS Name Service Messages
NetBIOS name service messages share a common structure. NetBIOS name service messages consist of the following:
• Name Service header. Fixed length (12 bytes long), containing information about the type of name service message and the numbers of the other records in the message.
• Question entries. Variable length for NetBIOS Name Registration, Refresh, or Release messages. This portion of the message contains the NetBIOS name being acted on by the message.
• Answer RRs. Variable length, containing resource records (RRs) returned in response to a question entry.
• Authority RRs. Variable length, containing RRs used to indicate the authority for the question being asked. These are not used by the WINS Server service in Windows Server 2008.
• Additional RRs. Variable length, containing other RRs that are not an answer to a question entry. This is almost the same structure as Domain Name System (DNS) Name Query Request and Response messages.
• Transaction ID. A 2-byte field that is used to identify a specific NetBIOS name service transaction. The sender of the request message creates the transaction ID and the responder copies it into the response message. This allows the WINS client to match the responses that it received from a WINS server with their requests. Each separate NetBIOS name service transaction has a different transaction ID. For example, if a WINS client is registering multiple names, each Name Registration Request message has a different transaction ID.
• Flags. A 2-byte field containing flags.
• Question Entry Count. A 2-byte field indicating the number of entries in the Question Entries section of the message. The sender of a request message always sets this value to 1 or more, although typically it is set at 1. The responder always sets this field to 0.
• Answer RR Count. A 2-byte field indicating the number of RRs in the Answer RRs section of the message. The sender of a request message sets this count to 0. The responder sets this to indicate the number of answers returned. This is typically 1 for unique NetBIOS name lookups and a larger number for Internet group name lookups.
• Authority RR Count. A 2-byte field indicating the number of RRs in the Authority RRs section of the message. Authority RRs are used for recursive NetBIOS name queries, which are not supported by the WINS Server service in Windows Server 2008. Therefore, this field is always set to 0 in NetBIOS name service messages to indicate that there are no authority RRs in the message.
• Additional RR Count. A 2-byte field indicating the number of RRs in the Additional RRs section of the NetBIOS name service message. These records are used when an RR needs to be included in any name service operation that is not a response to a name query request. For example, in a name release, an additional RR includes the name being released.
The fields within the Flags field are the following:
• Request/Response. A 1-bit field that is set to 0 for a request message or 1 for a response message.
• Operation Code. A 4-bit field that indicates the specific name service operation of the message. See Table 16-1 for a list of Operation Code values.
• Authoritative Answer. A 1-bit field that indicates, when set to 1 in a name query response, that the sender is authoritative for the NetBIOS name. For name service requests, this flag is always set to 0. For name service responses, the computer responding to the request sets it to 1 if it is authoritative for a NetBIOS name.
• Truncation. A 1-bit field that indicates, when set to 1 in a name query response, that the message was truncated because the original datagram containing the entire message exceeded 576 bytes. Similar to DNS truncation, RFC 1001 describes the use of TCP to obtain the original datagram. Windows Server 2008 and Windows Vista do not support
the use of TCP for NetBIOS name service messages. Therefore, the Truncation bit is always set to 0.
• Recursion Desired. A 1-bit field that indicates, when set to 1 in a name query request, that the query is recursive. When set to 0, the sender indicates an iterative query; the WINS server can return a list of other name servers that can be contacted to resolve the name. Windows Server 2008 and Windows Vista-based WINS clients set this flag to 1 for all name queries. If the flag is set to 1 in a name service message sent to a WINS server running Windows Server 2008, the WINS server sets it to 1 in the corresponding reply. Windows Server 2008 does not support iterative NetBIOS name queries.
• Recursion Available. A 1-bit field that indicates, when set to 1 in a name query response, that the WINS server can perform recursive queries. Set to 0 on all name request messages. The Windows Server 2008 WINS Server service sets this field to 1 in name service responses to indicate that it can perform recursive name query, name registration, and name release messages. If set to 0 in a response message, the client must iterate for name service queries and perform challenges for any name registrations.
• Reserved. A 2-bit field that is reserved and set to 0.
• Broadcast. A 1-bit field that indicates that the message is being sent as a broadcast (set to 1) or unicast (set to 0).
• Return Code. A 4-bit field that indicates the return code in a name query response. All name service requests set the value to 0. A return code of 0 in a name service response indicates a successful response (the answer is in the name query response message). A return code of 0 in name query responses means that the answer to the query is in the response message. A return code of 0 in name registrations means that the registration was successful.
Source of Information : Microsoft Press Windows Server 2008 TCP IP Protocols and Services
• Name Service header. Fixed length (12 bytes long), containing information about the type of name service message and the numbers of the other records in the message.
• Question entries. Variable length for NetBIOS Name Registration, Refresh, or Release messages. This portion of the message contains the NetBIOS name being acted on by the message.
• Answer RRs. Variable length, containing resource records (RRs) returned in response to a question entry.
• Authority RRs. Variable length, containing RRs used to indicate the authority for the question being asked. These are not used by the WINS Server service in Windows Server 2008.
• Additional RRs. Variable length, containing other RRs that are not an answer to a question entry. This is almost the same structure as Domain Name System (DNS) Name Query Request and Response messages.
• Transaction ID. A 2-byte field that is used to identify a specific NetBIOS name service transaction. The sender of the request message creates the transaction ID and the responder copies it into the response message. This allows the WINS client to match the responses that it received from a WINS server with their requests. Each separate NetBIOS name service transaction has a different transaction ID. For example, if a WINS client is registering multiple names, each Name Registration Request message has a different transaction ID.
• Flags. A 2-byte field containing flags.
• Question Entry Count. A 2-byte field indicating the number of entries in the Question Entries section of the message. The sender of a request message always sets this value to 1 or more, although typically it is set at 1. The responder always sets this field to 0.
• Answer RR Count. A 2-byte field indicating the number of RRs in the Answer RRs section of the message. The sender of a request message sets this count to 0. The responder sets this to indicate the number of answers returned. This is typically 1 for unique NetBIOS name lookups and a larger number for Internet group name lookups.
• Authority RR Count. A 2-byte field indicating the number of RRs in the Authority RRs section of the message. Authority RRs are used for recursive NetBIOS name queries, which are not supported by the WINS Server service in Windows Server 2008. Therefore, this field is always set to 0 in NetBIOS name service messages to indicate that there are no authority RRs in the message.
• Additional RR Count. A 2-byte field indicating the number of RRs in the Additional RRs section of the NetBIOS name service message. These records are used when an RR needs to be included in any name service operation that is not a response to a name query request. For example, in a name release, an additional RR includes the name being released.
The fields within the Flags field are the following:
• Request/Response. A 1-bit field that is set to 0 for a request message or 1 for a response message.
• Operation Code. A 4-bit field that indicates the specific name service operation of the message. See Table 16-1 for a list of Operation Code values.
• Authoritative Answer. A 1-bit field that indicates, when set to 1 in a name query response, that the sender is authoritative for the NetBIOS name. For name service requests, this flag is always set to 0. For name service responses, the computer responding to the request sets it to 1 if it is authoritative for a NetBIOS name.
• Truncation. A 1-bit field that indicates, when set to 1 in a name query response, that the message was truncated because the original datagram containing the entire message exceeded 576 bytes. Similar to DNS truncation, RFC 1001 describes the use of TCP to obtain the original datagram. Windows Server 2008 and Windows Vista do not support
the use of TCP for NetBIOS name service messages. Therefore, the Truncation bit is always set to 0.
• Recursion Desired. A 1-bit field that indicates, when set to 1 in a name query request, that the query is recursive. When set to 0, the sender indicates an iterative query; the WINS server can return a list of other name servers that can be contacted to resolve the name. Windows Server 2008 and Windows Vista-based WINS clients set this flag to 1 for all name queries. If the flag is set to 1 in a name service message sent to a WINS server running Windows Server 2008, the WINS server sets it to 1 in the corresponding reply. Windows Server 2008 does not support iterative NetBIOS name queries.
• Recursion Available. A 1-bit field that indicates, when set to 1 in a name query response, that the WINS server can perform recursive queries. Set to 0 on all name request messages. The Windows Server 2008 WINS Server service sets this field to 1 in name service responses to indicate that it can perform recursive name query, name registration, and name release messages. If set to 0 in a response message, the client must iterate for name service queries and perform challenges for any name registrations.
• Reserved. A 2-bit field that is reserved and set to 0.
• Broadcast. A 1-bit field that indicates that the message is being sent as a broadcast (set to 1) or unicast (set to 0).
• Return Code. A 4-bit field that indicates the return code in a name query response. All name service requests set the value to 0. A return code of 0 in a name service response indicates a successful response (the answer is in the name query response message). A return code of 0 in name query responses means that the answer to the query is in the response message. A return code of 0 in name registrations means that the registration was successful.
Source of Information : Microsoft Press Windows Server 2008 TCP IP Protocols and Services
NetBT Name Service Messages
WINS clients and WINS servers communicate by exchanging NetBT name service messages. NetBT messages and protocol operation are defined in RFCs 1001 and 1002. There are many types of NetBT name service messages defined in RFC 1002, which are typically sent as UDP messages. Both the WINS client and the WINS server listen on UDP port 137. The types of NetBT name service messages thatare the following:
• Name Query Request. Sent by a WINS client to a WINS server to perform NetBIOS name resolution.
• Name Query Response. Sent by a WINS server to a WINS client to respond to a name query request. There is a positive name query response and a negative name query response.
• Name Registration Request Sent by a WINS client to a WINS server to perform name registration.
• Name Registration Response. Sent by a WINS server to a WINS client to respond to a name registration request. There is a positive name registration response and a negative name registration response.
• Wait Acknowledgment. Sent by a WINS server to a WINS client during name registration when confirming the ownership of an existing name previously registered by another client.
• Name Refresh Request. Sent by a WINS client to a WINS server to refresh a name that was previously registered. The response to a name refresh request is a name registration response.
• Name Release Request. Sent by a WINS client to a WINS server to release the registration of a name that was previously registered.
• Name Release Response. Sent by a WINS server to a WINS client to respond to a name release request. There is a positive name release response and a negative name release response.
Source of Information : Microsoft Press Windows Server 2008 TCP IP Protocols and Services
• Name Query Request. Sent by a WINS client to a WINS server to perform NetBIOS name resolution.
• Name Query Response. Sent by a WINS server to a WINS client to respond to a name query request. There is a positive name query response and a negative name query response.
• Name Registration Request Sent by a WINS client to a WINS server to perform name registration.
• Name Registration Response. Sent by a WINS server to a WINS client to respond to a name registration request. There is a positive name registration response and a negative name registration response.
• Wait Acknowledgment. Sent by a WINS server to a WINS client during name registration when confirming the ownership of an existing name previously registered by another client.
• Name Refresh Request. Sent by a WINS client to a WINS server to refresh a name that was previously registered. The response to a name refresh request is a name registration response.
• Name Release Request. Sent by a WINS client to a WINS server to release the registration of a name that was previously registered.
• Name Release Response. Sent by a WINS server to a WINS client to respond to a name release request. There is a positive name release response and a negative name release response.
Source of Information : Microsoft Press Windows Server 2008 TCP IP Protocols and Services
Understanding WINS and NetBIOS
The Network Basic Input/Output System (NetBIOS) was developed in 1983 and used by IBM as a way for computer applications to communicate over a network. NetBIOS is also firmly ingrained into all Microsoft operating systems that have come before the Windows 2000 series. Legacy software applications may also rely on NetBIOS for locating resources on the network.
NetBIOS provides a way for identifying resources on a network (such as a printer, file server, and so on). All devices running on the network are assigned a unique 16-byte name that defines the particular computer or printer to the network (or a service on a computer—this means that a single computer may provide services identified by different NetBIOS names). NetBIOS names are typically assigned when you install a particular operating system on a computer. Down-level operating systems such as Windows NT all request that a unique, 15-character NetBIOS name be entered for the computer during the installation process of the OS. When you install Windows on a computer, a computer name is created for that computer. If you change the hostname and the name is fewer than 15 characters, it also becomes the NetBIOS name for the computer (otherwise, the hostname is truncated to a 15-character NetBIOS name).
In fact, NetBIOS names are 16 characters long. The last character is used by the computer's operating system to specify the special functions of certain computers such as domain controllers and browsers.
Even though the default networking protocol for Windows Server 2008 is TCP/IP and the primary name-resolution strategy is DNS, an important issue related to NetBIOS names rears its head on your Windows Server 2008 domain. Applications that still use NetBIOS for identifying other computers and resources on the network must have a way of resolving these NetBIOS names to IP addresses. This process is cleverly called NetBIOS name resolution. NetBIOS is also required in the networking environment for NetBIOS dependent applications.
NetBIOS Broadcasts
When a computer seeks to resolve a NetBIOS name to an IP address, it sends a NetBIOS broadcast. Because the name-resolution request takes the form of a broadcast message, it is sent to all nodes on the local subnet (the subnet being a particular segment on a routed network).
For example, imagine a computer named Kirk wants to send data to a computer named Spock. Kirk broadcasts that it would like to send data to Spock but does not know Spock's IP address. When Spock hears this broadcast (as do all nodes on the subnet), Spock sends a response providing Kirk with the IP address. Kirk can now proceed with establishing a network session with Spock and transferring data as needed.
Two obvious problems plague the use of broadcasts for NetBIOS name resolution. First, the broadcast messages clog your network with broadcast traffic, which sucks up your bandwidth. Another problem is that broadcast messages are not typically forwarded by routers on the network (unless the router has also been configured as a bridge). So, if a computer on one subnet uses a broadcast message to resolve a NetBIOS name for a computer that is on another subnet, the broadcast message is never forwarded to the intended target.
One strategy that has been worked out to cut down on the number of broadcast messages is as follows: After a computer has discovered the IP addresses of other computers on the segment through the use of broadcasts, these IP addresses are kept in a NetBIOS name cache on that computer. This cuts down on broadcasts in the case of "repeat" business with a particular computer or computers on the network. You can view the NetBIOS name cache on a computer running Windows Server 2008 by using the NBTSTAT command. We discuss this command-line tool later in the hour.
Working with LMHOSTS Files
Another alternative for NetBIOS name resolution is to use an LMHOSTS file. The LMHOSTS file is a text file that lists the IP addresses of computers on the network followed by their NetBIOS name. LMHOSTS files are static and must be updated by the network administrator (that means you). And although they provide the computer with a quick way to look up an IP address based on a NetBIOS name, you must place them on each computer on the network (and whenever you add computers to the network, you also have to update all the LMHOSTS files on all the computers).
Some network administrators still use LMHOSTS files to resolve NetBIOS names to IP addresses on their networks. On a server running Windows Server 2008, the LMHOSTS file is kept in the \Windows\system32\drivers\etc folder. The basic structure of an LMHOSTS file is a two-column text file:
IP address NetBIOS name
Windows 2008 actually provides a sample LMHOSTS file in the \windows\system32\drivers\etc folder. You can open it using Windows Notepad or another text editor.
Included in the Windows 2008 LMHOSTS file are explicit directions for building your own LMHOSTS lists. Pay special attention to the fact that descriptive entries in the file are always followed by the number sign (#). All other entries are read as mapping records.
The major problem with LMHOSTS files is that they represent a fairly labor-intensive way to manage NetBIOS name resolution. If LMHOSTS files have been used on the network in the past, however, they can be integrated into the WINS database on your WINS server. An Import LMHOSTS File command is available on the WINS snap-in Action menu. We discuss the WINS snap-in later in the hour.
NetBIOS Node Types
Before concentrating on the Windows Server 2008 WINS service and its installation and configuration, it is important to discuss the different node types that can exist in the NetBIOS environment. A node type simply refers to the way that a computer on the network registers with a NetBIOS name server (such as WINS) and seeks to resolve NetBIOS names to IP addresses. There are four node types:
B The client uses broadcast messages for name registration and name resolution.
P The client uses unicast (directly to the server's IP address) messages to a NetBIOS name server for both name registration and NetBIOS name resolution.
H A hybrid node type, these clients use unicast messages to the NetBIOS name server for registration and resolution. If they cannot find a NetBIOS name server (a WINS server), the client resorts to broadcast messages for registration and resolution.
M Clients use broadcasts for name registration and for name resolution. However, if the name cannot be resolved by broadcast, the client attempts to contact a NetBIOS name server.
Windows 2008 WINS clients (those configured for WINS) act as H nodes. They attempts to resolve names by using the WINS server first, and then they resort to broadcasts if a WINS server is not available. As a last resort, these clients consult their LMHOSTS file if one is available locally.
Deploying a WINS Server
The most foolproof method for dealing with NetBIOS naming issues is to deploy a WINS server (or servers) on your network. WINS provides the greatest amount of efficiency in terms of your network bandwidth. The series of steps that allows a WINS client to take advantage of the WINS server for NetBIOS name resolution is very straightforward:
1. When a WINS client computer boots up, it registers its NetBIOS name and IP address with the WINS server.
2. When a WINS client on the network wants to communicate with a network resource designated by a particular NetBIOS name, it communicates with the WINS server to handle the NetBIOS name resolution of its intended target, rather than sending out a broadcast to all nodes on the segment.
3. The WINS server finds the appropriate mapping of NetBIOS-name-to-IP-address in its database and returns the IP address to the WINS client.
4. If the WINS client cannot contact the primary WINS server, the client makes two more attempts to contact the primary WINS server. Then it attempts to contact the secondary WINS server if one has been designated in the TCP/IP properties for the client (or if the client is a DHCP client with multiple WINS servers configured).
5. If the secondary WINS server (or other WINS server because the client attempts to contact WINS servers in the order designated in the TCP/IP properties) can handle the request, no problem. However, if the client cannot contact any designated WINS server, the client resorts to a network broadcast. If a number of WINS servers are available on the network, the chances of the client having to resort to a broadcast message are slim.
The great thing about WINS is that the database compiled by the server is dynamic. The WINS clients actually register with the server, supplying the entries in the WINS database. This is similar to the way that Dynamic DNS (DDNS) works, however WINS does not provide a mechanism for secure updates as DDNS does. Any computer configured to use a WINS server can register itself in the WINS database.
Source of Information : Sams Teach Yourself Windows Server 2008
NetBIOS provides a way for identifying resources on a network (such as a printer, file server, and so on). All devices running on the network are assigned a unique 16-byte name that defines the particular computer or printer to the network (or a service on a computer—this means that a single computer may provide services identified by different NetBIOS names). NetBIOS names are typically assigned when you install a particular operating system on a computer. Down-level operating systems such as Windows NT all request that a unique, 15-character NetBIOS name be entered for the computer during the installation process of the OS. When you install Windows on a computer, a computer name is created for that computer. If you change the hostname and the name is fewer than 15 characters, it also becomes the NetBIOS name for the computer (otherwise, the hostname is truncated to a 15-character NetBIOS name).
In fact, NetBIOS names are 16 characters long. The last character is used by the computer's operating system to specify the special functions of certain computers such as domain controllers and browsers.
Even though the default networking protocol for Windows Server 2008 is TCP/IP and the primary name-resolution strategy is DNS, an important issue related to NetBIOS names rears its head on your Windows Server 2008 domain. Applications that still use NetBIOS for identifying other computers and resources on the network must have a way of resolving these NetBIOS names to IP addresses. This process is cleverly called NetBIOS name resolution. NetBIOS is also required in the networking environment for NetBIOS dependent applications.
NetBIOS Broadcasts
When a computer seeks to resolve a NetBIOS name to an IP address, it sends a NetBIOS broadcast. Because the name-resolution request takes the form of a broadcast message, it is sent to all nodes on the local subnet (the subnet being a particular segment on a routed network).
For example, imagine a computer named Kirk wants to send data to a computer named Spock. Kirk broadcasts that it would like to send data to Spock but does not know Spock's IP address. When Spock hears this broadcast (as do all nodes on the subnet), Spock sends a response providing Kirk with the IP address. Kirk can now proceed with establishing a network session with Spock and transferring data as needed.
Two obvious problems plague the use of broadcasts for NetBIOS name resolution. First, the broadcast messages clog your network with broadcast traffic, which sucks up your bandwidth. Another problem is that broadcast messages are not typically forwarded by routers on the network (unless the router has also been configured as a bridge). So, if a computer on one subnet uses a broadcast message to resolve a NetBIOS name for a computer that is on another subnet, the broadcast message is never forwarded to the intended target.
One strategy that has been worked out to cut down on the number of broadcast messages is as follows: After a computer has discovered the IP addresses of other computers on the segment through the use of broadcasts, these IP addresses are kept in a NetBIOS name cache on that computer. This cuts down on broadcasts in the case of "repeat" business with a particular computer or computers on the network. You can view the NetBIOS name cache on a computer running Windows Server 2008 by using the NBTSTAT command. We discuss this command-line tool later in the hour.
Working with LMHOSTS Files
Another alternative for NetBIOS name resolution is to use an LMHOSTS file. The LMHOSTS file is a text file that lists the IP addresses of computers on the network followed by their NetBIOS name. LMHOSTS files are static and must be updated by the network administrator (that means you). And although they provide the computer with a quick way to look up an IP address based on a NetBIOS name, you must place them on each computer on the network (and whenever you add computers to the network, you also have to update all the LMHOSTS files on all the computers).
Some network administrators still use LMHOSTS files to resolve NetBIOS names to IP addresses on their networks. On a server running Windows Server 2008, the LMHOSTS file is kept in the \Windows\system32\drivers\etc folder. The basic structure of an LMHOSTS file is a two-column text file:
IP address NetBIOS name
Windows 2008 actually provides a sample LMHOSTS file in the \windows\system32\drivers\etc folder. You can open it using Windows Notepad or another text editor.
Included in the Windows 2008 LMHOSTS file are explicit directions for building your own LMHOSTS lists. Pay special attention to the fact that descriptive entries in the file are always followed by the number sign (#). All other entries are read as mapping records.
The major problem with LMHOSTS files is that they represent a fairly labor-intensive way to manage NetBIOS name resolution. If LMHOSTS files have been used on the network in the past, however, they can be integrated into the WINS database on your WINS server. An Import LMHOSTS File command is available on the WINS snap-in Action menu. We discuss the WINS snap-in later in the hour.
NetBIOS Node Types
Before concentrating on the Windows Server 2008 WINS service and its installation and configuration, it is important to discuss the different node types that can exist in the NetBIOS environment. A node type simply refers to the way that a computer on the network registers with a NetBIOS name server (such as WINS) and seeks to resolve NetBIOS names to IP addresses. There are four node types:
B The client uses broadcast messages for name registration and name resolution.
P The client uses unicast (directly to the server's IP address) messages to a NetBIOS name server for both name registration and NetBIOS name resolution.
H A hybrid node type, these clients use unicast messages to the NetBIOS name server for registration and resolution. If they cannot find a NetBIOS name server (a WINS server), the client resorts to broadcast messages for registration and resolution.
M Clients use broadcasts for name registration and for name resolution. However, if the name cannot be resolved by broadcast, the client attempts to contact a NetBIOS name server.
Windows 2008 WINS clients (those configured for WINS) act as H nodes. They attempts to resolve names by using the WINS server first, and then they resort to broadcasts if a WINS server is not available. As a last resort, these clients consult their LMHOSTS file if one is available locally.
Deploying a WINS Server
The most foolproof method for dealing with NetBIOS naming issues is to deploy a WINS server (or servers) on your network. WINS provides the greatest amount of efficiency in terms of your network bandwidth. The series of steps that allows a WINS client to take advantage of the WINS server for NetBIOS name resolution is very straightforward:
1. When a WINS client computer boots up, it registers its NetBIOS name and IP address with the WINS server.
2. When a WINS client on the network wants to communicate with a network resource designated by a particular NetBIOS name, it communicates with the WINS server to handle the NetBIOS name resolution of its intended target, rather than sending out a broadcast to all nodes on the segment.
3. The WINS server finds the appropriate mapping of NetBIOS-name-to-IP-address in its database and returns the IP address to the WINS client.
4. If the WINS client cannot contact the primary WINS server, the client makes two more attempts to contact the primary WINS server. Then it attempts to contact the secondary WINS server if one has been designated in the TCP/IP properties for the client (or if the client is a DHCP client with multiple WINS servers configured).
5. If the secondary WINS server (or other WINS server because the client attempts to contact WINS servers in the order designated in the TCP/IP properties) can handle the request, no problem. However, if the client cannot contact any designated WINS server, the client resorts to a network broadcast. If a number of WINS servers are available on the network, the chances of the client having to resort to a broadcast message are slim.
The great thing about WINS is that the database compiled by the server is dynamic. The WINS clients actually register with the server, supplying the entries in the WINS database. This is similar to the way that Dynamic DNS (DDNS) works, however WINS does not provide a mechanism for secure updates as DDNS does. Any computer configured to use a WINS server can register itself in the WINS database.
Source of Information : Sams Teach Yourself Windows Server 2008
Virtual Folders
Let’s step back a bit before diving too deeply into potentially confusing territory. In order to understand Vista’s virtual folders, it’s important to first understand the thinking that went into this feature; and because this is the ever-delayed Windows Vista I’m talking about, it might also be helpful to know about Microsoft’s original plans for the Vista shell and virtual folders and compare those plans with what eventually happened.
Microsoft originally decided not to include in Vista a traditional file system with drive letters, physical file-system paths, and real folders. The software giant wanted to virtualize the entire file system so that you wouldn’t need to worry about such arcane things as “the root of C:” and the Program Files folder. Instead, you would just access your documents and applications without ever thinking about where they resided on the disk. After all, that sort of electronic housekeeping is what a computer is good at, right?
This original vision required a healthy dose of technology. The core piece of this technology would be a new storage engine called WinFS (short for Windows Future Storage), which would have combined the best features of the NTFS file system with the relational database functionality of Microsoft’s SQL Server products. As of this writing, Microsoft has been working on WinFS, and its predecessors, for about a decade.
Unfortunately, the WinFS technology wasn’t even close to being ready in time for
Windows Vista, so Microsoft pulled WinFS out of Vista and began developing it separately from the OS. Ultimately, it completely canceled plans to ship WinFS as a separate product. Instead, WinFS technologies will be integrated into future Windows versions and other Microsoft products.
Even though WinFS was out of the picture, Microsoft figured it could deliver much of that system’s benefits using an updated version of the file system indexer it has shipped in Windows for years; and for about a year of Vista’s development in 2004–2005, that was the plan. Instead of special shell folders such as Documents, users would access virtual folders such as All Documents, which would aggregate all of the documents on the hard drive and present them in a single location. Other special shell folders, such as Pictures and Music, would also be replaced by virtual folders.
Problem solved, right? Wrong. Beta testers—who are presumably more technical than most PC users—found the transition from normal folders to virtual folders to be extremely confusing. In retrospect, this should have been obvious. After all, a virtual folder that displays all of your documents is kind of useful when you’re looking for something, but where do you save a new file? Is a virtual folder even a real place for applications that want to save data? And do users need to understand the differences between normal folders and virtual folders? Why have both kinds of folders?
With the delays mounting, Microsoft retreated from the virtual-folder scheme, just as it had when it stripped out WinFS previously. That’s why the file system you see in Windows Vista is actually quite similar to that in Windows XP and previous Windows versions. That is, the file system still uses drive letters, normal folders, and special shell folders such as Documents and Pictures. If you’re familiar with any prior Windows version, you should feel right at home in the Vista shell. (Likewise, if you’ve found the Windows file system to be a bit, well, lackluster, all the same complaints still apply in Vista.)
There’s one major difference between Vista’s file system and that of previous Windows versions, although it’s not particularly obvious. Even though Microsoft has decided not to replace special shell folders with virtual folders in this release, the company is still shipping virtual-folder technology in Windows Vista. The idea is that users will get used to virtual folders now, and then perhaps a future Windows version will simply move to that system, and eventually we’ll all reach some nerdvana where all the silly file-system constructs used today are suddenly passé.
In short, virtual folders do exist in Windows Vista; they’re just somewhat hidden. OK, they’re really well hidden, maybe even devilishly well hidden. That makes them a power-user feature and thus, for readers of this book, inherently interesting. Most people won’t even discover virtual folders and their contained shared searches. In fact, if you want to harness some of the most awesome and unique technology in Windows Vista, this is the place to start; the skills you learn now will give you a leg up when Microsoft finally gets around to retiring the current file system. It’s only a matter of time.
Source of Information : Wiley Windows Vista Secrets SP1 Edition
Microsoft originally decided not to include in Vista a traditional file system with drive letters, physical file-system paths, and real folders. The software giant wanted to virtualize the entire file system so that you wouldn’t need to worry about such arcane things as “the root of C:” and the Program Files folder. Instead, you would just access your documents and applications without ever thinking about where they resided on the disk. After all, that sort of electronic housekeeping is what a computer is good at, right?
This original vision required a healthy dose of technology. The core piece of this technology would be a new storage engine called WinFS (short for Windows Future Storage), which would have combined the best features of the NTFS file system with the relational database functionality of Microsoft’s SQL Server products. As of this writing, Microsoft has been working on WinFS, and its predecessors, for about a decade.
Unfortunately, the WinFS technology wasn’t even close to being ready in time for
Windows Vista, so Microsoft pulled WinFS out of Vista and began developing it separately from the OS. Ultimately, it completely canceled plans to ship WinFS as a separate product. Instead, WinFS technologies will be integrated into future Windows versions and other Microsoft products.
Even though WinFS was out of the picture, Microsoft figured it could deliver much of that system’s benefits using an updated version of the file system indexer it has shipped in Windows for years; and for about a year of Vista’s development in 2004–2005, that was the plan. Instead of special shell folders such as Documents, users would access virtual folders such as All Documents, which would aggregate all of the documents on the hard drive and present them in a single location. Other special shell folders, such as Pictures and Music, would also be replaced by virtual folders.
Problem solved, right? Wrong. Beta testers—who are presumably more technical than most PC users—found the transition from normal folders to virtual folders to be extremely confusing. In retrospect, this should have been obvious. After all, a virtual folder that displays all of your documents is kind of useful when you’re looking for something, but where do you save a new file? Is a virtual folder even a real place for applications that want to save data? And do users need to understand the differences between normal folders and virtual folders? Why have both kinds of folders?
With the delays mounting, Microsoft retreated from the virtual-folder scheme, just as it had when it stripped out WinFS previously. That’s why the file system you see in Windows Vista is actually quite similar to that in Windows XP and previous Windows versions. That is, the file system still uses drive letters, normal folders, and special shell folders such as Documents and Pictures. If you’re familiar with any prior Windows version, you should feel right at home in the Vista shell. (Likewise, if you’ve found the Windows file system to be a bit, well, lackluster, all the same complaints still apply in Vista.)
There’s one major difference between Vista’s file system and that of previous Windows versions, although it’s not particularly obvious. Even though Microsoft has decided not to replace special shell folders with virtual folders in this release, the company is still shipping virtual-folder technology in Windows Vista. The idea is that users will get used to virtual folders now, and then perhaps a future Windows version will simply move to that system, and eventually we’ll all reach some nerdvana where all the silly file-system constructs used today are suddenly passé.
In short, virtual folders do exist in Windows Vista; they’re just somewhat hidden. OK, they’re really well hidden, maybe even devilishly well hidden. That makes them a power-user feature and thus, for readers of this book, inherently interesting. Most people won’t even discover virtual folders and their contained shared searches. In fact, if you want to harness some of the most awesome and unique technology in Windows Vista, this is the place to start; the skills you learn now will give you a leg up when Microsoft finally gets around to retiring the current file system. It’s only a matter of time.
Source of Information : Wiley Windows Vista Secrets SP1 Edition
Windows Vista Special Shell Folders
Most Windows Vista Secrets readers are probably familiar with basic computer file system concepts such as files, folders, and drive letters; but you may not realize that certain locations in the Windows shell—that is, Windows Explorer, the application with which you literally explore the contents of your PC’s hard drives—have been specially configured to work with particular data types, and live in the shell hierarchy outside of their physical locations. In Windows XP and previous Windows versions, these locations were called special shell folders, and they included such things as My Documents, My Pictures, and My Music.
In Windows Vista these special shell folders still exist, but now most of them have different names and are accompanied by a number of new members. They’re also in a different location: Whereas Windows XP placed user folders (which contain the special shell folders for each user) in C:\Documents and Settings\Your_User_Name by default, Windows Vista uses the simpler C:\Users\Your_User_Name.
Special Shell Folders
Home. This special location is named after your user name. If you chose the user name Paul, for example, then your Home folder would be named Paul as well. (Case matters: If you enter paul, it will be paul and not Paul.) This folder is available as the top option on the right-hand, fixed part of the Start Menu. Although it was never particularly obvious, every user actually had a Home folder in previous Windows versions.
Contacts. A new addition to Windows Vista, Contacts acts as a central database for Vista’s centralized contacts management, which is used by Windows Mail and can be used by any third-party application.
Desktop. This folder represents your Windows Vista desktop. Any folders, files, or shortcuts you place on the desktop appear in this folder too (and vice versa). There’s one exception: If you enable certain desktop icons—such as Computer, User’s Files, Network, Recycle Bin, or Control Panel—via the Desktop Icon Settings dialog, these icons will not appear in the Desktop folder.
Documents. A replacement for My Documents, this folder is specially configured to handle various document types, such as Word documents, text fi les, and the like. As with
its predecessor, Documents is the default location for the Save and Save As dialog boxes in most applications.
Downloads. New to Windows Vista, this folder is the default location for files downloaded from the Web with Internet Explorer and other Web browsers, including Mozilla Firefox.
Favorites. A central repository for your Internet Explorer Favorites (or what other browsers typically call Bookmarks). The Favorites folder has been in Windows for several years.
Links. New to Windows Vista, this folder typically contains shortcuts to common shell locations. Its contents appear in the Favorite Links pane of Windows Explorer windows. Note that only shortcuts to folder and other shell locations appear in Favorite Links. If you copy a shortcut to a document here, for example, it will not appear in the list.
Saved Games. A new addition to Windows Vista, the Saved Games folder is designed as a place for Vista-compatible game titles to store saved game information.
Pictures. A replacement for My Pictures. The Pictures folder is designed to handle digital photographs and other picture fi les and to work in tandem with other photorelated tools in Vista, such as Windows Photo Gallery and the Import Pictures and Videos Wizard.
Music. A replacement for XP’s My Music folder. The Music folder is designed to work with digital music and other audio fi les. If you rip music from an audio CD or purchase music from an online music service such as the Apple iTunes Store or Amazon MP3, those fi les are typically saved to your Music folder by default.
Searches. New to Windows Vista, this folder contains built-in and user-created saved searches.
Videos. A replacement for My Videos. This folder is designed to store digital videos of any kind, including home movies. It also interacts with video-oriented tools in Vista, such as Windows Movie Maker and Windows DVD Maker. In Windows XP you had to run Windows Movie Maker once before the My Videos folder would appear. This is no longer the case in Windows Vista, where the new Videos folder is always available under each user’s Home folder. However, as with XP, it’s still impossible to add a link to the Videos folder to the right side of the Start Menu. The Videos folder, it seems, is still a second-class citizen in Microsoft’s eyes.
Each of the special shell folders in Windows Vista shares certain characteristics. First, they are all physical folders in the sense that they are represented by a specific location in the Windows shell hierarchy. For example, your Home folder is now found at C:\Users\username by default. Likewise, Documents can be found at C:\Users\username\Documents.
You might notice that most folder names (Saved Games is a curious exception)—and indeed the names of the folders above each of them in the shell path—has been stripped of spaces. That is, each folder is now a single word (e.g., Documents instead of My Documents). That’s because of a renewed commitment to shell scripting in Windows Vista, an environment in which it’s simply harder to deal with spaces.
Finally, many of the special shell folders are represented somewhat differently in the Windows shell than are other folders, which you might think of as normal physical folders.
The Documents, Favorites, Music, and Pictures folders are all colored blue-green now instead of the normal yellow folder color; and although you can create a folder almost anywhere you’d like in the Windows Vista shell—assuming you have the security credentials to do so—special shell folders are typically found only in their preset locations within the file system.
In addition to the new special shell folders in Vista, there are also some differences in the way that preexisting special shell folders are organized now. For example, folders such as My Pictures, My Music, and My Videos were physically arranged below (and logically contained within) the My Documents folder in previous Windows versions; but in Windows Vista the new versions of these folders are found directly below each user’s Home folder, alongside Documents. This won’t affect typical users, who will likely access special shell folders like My Documents and My Pictures only from the Start Menu, but more advanced users will want to be aware of the changes.
Advanced users can use the Registry Editor (regedit.exe) to change special shell-folder locations. (If you’re not familiar with the Registry, this isn’t the time to start. You can irreperably harm Windows via the Registry.) Using regedit, navigate to HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\ Explorer\Shell Folders. You’ll see a variety of special shell folders listed there, including Personal (Documents), My Music (Music), My Pictures (Pictures), and My Video (Videos). To change the location of one of these special folders, simply double-click in regedit and add the new location to the Value data field in the dialog that appears.
You can see some of Vista’s special folders in your Start Menu, but if you want a better idea of how they’re laid out in the fi le system, simply launch Windows Explorer and enable the classic left-mounted folder hierarchy, which is now found in the bottom-left corner of the window. The new Home folder layout is actually quite similar to that used by Unix and Linux systems, including Apple’s Mac OS X. Vista even follows the same naming conventions these competitors utilize.
Source of information : Wiley Windows Vista Secrets SP1 Edition
In Windows Vista these special shell folders still exist, but now most of them have different names and are accompanied by a number of new members. They’re also in a different location: Whereas Windows XP placed user folders (which contain the special shell folders for each user) in C:\Documents and Settings\Your_User_Name by default, Windows Vista uses the simpler C:\Users\Your_User_Name.
Special Shell Folders
Home. This special location is named after your user name. If you chose the user name Paul, for example, then your Home folder would be named Paul as well. (Case matters: If you enter paul, it will be paul and not Paul.) This folder is available as the top option on the right-hand, fixed part of the Start Menu. Although it was never particularly obvious, every user actually had a Home folder in previous Windows versions.
Contacts. A new addition to Windows Vista, Contacts acts as a central database for Vista’s centralized contacts management, which is used by Windows Mail and can be used by any third-party application.
Desktop. This folder represents your Windows Vista desktop. Any folders, files, or shortcuts you place on the desktop appear in this folder too (and vice versa). There’s one exception: If you enable certain desktop icons—such as Computer, User’s Files, Network, Recycle Bin, or Control Panel—via the Desktop Icon Settings dialog, these icons will not appear in the Desktop folder.
Documents. A replacement for My Documents, this folder is specially configured to handle various document types, such as Word documents, text fi les, and the like. As with
its predecessor, Documents is the default location for the Save and Save As dialog boxes in most applications.
Downloads. New to Windows Vista, this folder is the default location for files downloaded from the Web with Internet Explorer and other Web browsers, including Mozilla Firefox.
Favorites. A central repository for your Internet Explorer Favorites (or what other browsers typically call Bookmarks). The Favorites folder has been in Windows for several years.
Links. New to Windows Vista, this folder typically contains shortcuts to common shell locations. Its contents appear in the Favorite Links pane of Windows Explorer windows. Note that only shortcuts to folder and other shell locations appear in Favorite Links. If you copy a shortcut to a document here, for example, it will not appear in the list.
Saved Games. A new addition to Windows Vista, the Saved Games folder is designed as a place for Vista-compatible game titles to store saved game information.
Pictures. A replacement for My Pictures. The Pictures folder is designed to handle digital photographs and other picture fi les and to work in tandem with other photorelated tools in Vista, such as Windows Photo Gallery and the Import Pictures and Videos Wizard.
Music. A replacement for XP’s My Music folder. The Music folder is designed to work with digital music and other audio fi les. If you rip music from an audio CD or purchase music from an online music service such as the Apple iTunes Store or Amazon MP3, those fi les are typically saved to your Music folder by default.
Searches. New to Windows Vista, this folder contains built-in and user-created saved searches.
Videos. A replacement for My Videos. This folder is designed to store digital videos of any kind, including home movies. It also interacts with video-oriented tools in Vista, such as Windows Movie Maker and Windows DVD Maker. In Windows XP you had to run Windows Movie Maker once before the My Videos folder would appear. This is no longer the case in Windows Vista, where the new Videos folder is always available under each user’s Home folder. However, as with XP, it’s still impossible to add a link to the Videos folder to the right side of the Start Menu. The Videos folder, it seems, is still a second-class citizen in Microsoft’s eyes.
Each of the special shell folders in Windows Vista shares certain characteristics. First, they are all physical folders in the sense that they are represented by a specific location in the Windows shell hierarchy. For example, your Home folder is now found at C:\Users\username by default. Likewise, Documents can be found at C:\Users\username\Documents.
You might notice that most folder names (Saved Games is a curious exception)—and indeed the names of the folders above each of them in the shell path—has been stripped of spaces. That is, each folder is now a single word (e.g., Documents instead of My Documents). That’s because of a renewed commitment to shell scripting in Windows Vista, an environment in which it’s simply harder to deal with spaces.
Finally, many of the special shell folders are represented somewhat differently in the Windows shell than are other folders, which you might think of as normal physical folders.
The Documents, Favorites, Music, and Pictures folders are all colored blue-green now instead of the normal yellow folder color; and although you can create a folder almost anywhere you’d like in the Windows Vista shell—assuming you have the security credentials to do so—special shell folders are typically found only in their preset locations within the file system.
In addition to the new special shell folders in Vista, there are also some differences in the way that preexisting special shell folders are organized now. For example, folders such as My Pictures, My Music, and My Videos were physically arranged below (and logically contained within) the My Documents folder in previous Windows versions; but in Windows Vista the new versions of these folders are found directly below each user’s Home folder, alongside Documents. This won’t affect typical users, who will likely access special shell folders like My Documents and My Pictures only from the Start Menu, but more advanced users will want to be aware of the changes.
Advanced users can use the Registry Editor (regedit.exe) to change special shell-folder locations. (If you’re not familiar with the Registry, this isn’t the time to start. You can irreperably harm Windows via the Registry.) Using regedit, navigate to HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\ Explorer\Shell Folders. You’ll see a variety of special shell folders listed there, including Personal (Documents), My Music (Music), My Pictures (Pictures), and My Video (Videos). To change the location of one of these special folders, simply double-click in regedit and add the new location to the Value data field in the dialog that appears.
You can see some of Vista’s special folders in your Start Menu, but if you want a better idea of how they’re laid out in the fi le system, simply launch Windows Explorer and enable the classic left-mounted folder hierarchy, which is now found in the bottom-left corner of the window. The new Home folder layout is actually quite similar to that used by Unix and Linux systems, including Apple’s Mac OS X. Vista even follows the same naming conventions these competitors utilize.
Source of information : Wiley Windows Vista Secrets SP1 Edition
Windows Aero
Windows Aero is the premium user experience in Windows Vista and the one most users will want to access. It provides a number of unique features. First, Windows Aero enables the new Aero Glass look and feel in which the Start Menu, the taskbar, and all onscreen windows and dialog boxes take on a new glass-like translucent sheen
Aero Glass is designed to move the visual focus away from the windows themselves and to the content they contain. Whether that effort is successful is open to debate, but it’s certainly true that window borders have lost the vast, dark-colored title bars of previous Windows versions and provide a softer-looking and more organic-looking container around window contents. Compare Windows XP’s My Computer window to Windows Vista’s Computer window.
When you have a lot of Aero windows open onscreen, it’s often hard to tell which one is on top or has the focus. Typically, that window will have a bright red Close window button, whereas other windows will not.
When you utilize the Windows Aero user experience, you receive other benefits. Certain
Windows Vista features, for example, are available only when you’re using Aero. Windows Flip and Flip 3D, two new task-switching features, are available only in Aero.
Windows Flip and Flip 3D are most typically accessed via keyboard shortcuts. The trick, of course, is that you have to know those shortcuts. To use Windows Flip, hold down the Alt key and press the Tab key to cycle between all of the running applications and open windows. To use Flip 3D, hold down the Windows key and press the Tab key to cycle between these windows.
Aero also enables dynamic window animations, so that when you minimize a window to the taskbar, it subtly animates to show you exactly where it went. This kind of functionality was actually first introduced in Windows 95, but it has been made more subtle and fluid in Windows Vista. Additionally, Aero enables live taskbar thumbnails: When you mouse over buttons in the taskbar, a small thumbnail preview will pop up, showing you the window without actually activating it first.
In addition to its obvious visual charms, Windows Aero also offers lower-level improvements that provide a more reliable desktop experience than you might be used to with previous Windows versions. Thanks to a new graphics architecture based on DirectX video-game libraries, Windows Vista can move windows across the screen without any of the visual tearing or glitches that were common in Windows XP. The effect is most prominent in windows with animated content, such as when you’re playing a video in Windows Media Player (WMP). But it’s not just about looks. Windows Aero is simply more reliable than the other user experiences. To understand why that’s so, you need to examine Aero’s strict hardware and software requirements.
Source of information : Wiley Windows Vista Secrets SP1 Edition
Aero Glass is designed to move the visual focus away from the windows themselves and to the content they contain. Whether that effort is successful is open to debate, but it’s certainly true that window borders have lost the vast, dark-colored title bars of previous Windows versions and provide a softer-looking and more organic-looking container around window contents. Compare Windows XP’s My Computer window to Windows Vista’s Computer window.
When you have a lot of Aero windows open onscreen, it’s often hard to tell which one is on top or has the focus. Typically, that window will have a bright red Close window button, whereas other windows will not.
When you utilize the Windows Aero user experience, you receive other benefits. Certain
Windows Vista features, for example, are available only when you’re using Aero. Windows Flip and Flip 3D, two new task-switching features, are available only in Aero.
Windows Flip and Flip 3D are most typically accessed via keyboard shortcuts. The trick, of course, is that you have to know those shortcuts. To use Windows Flip, hold down the Alt key and press the Tab key to cycle between all of the running applications and open windows. To use Flip 3D, hold down the Windows key and press the Tab key to cycle between these windows.
Aero also enables dynamic window animations, so that when you minimize a window to the taskbar, it subtly animates to show you exactly where it went. This kind of functionality was actually first introduced in Windows 95, but it has been made more subtle and fluid in Windows Vista. Additionally, Aero enables live taskbar thumbnails: When you mouse over buttons in the taskbar, a small thumbnail preview will pop up, showing you the window without actually activating it first.
In addition to its obvious visual charms, Windows Aero also offers lower-level improvements that provide a more reliable desktop experience than you might be used to with previous Windows versions. Thanks to a new graphics architecture based on DirectX video-game libraries, Windows Vista can move windows across the screen without any of the visual tearing or glitches that were common in Windows XP. The effect is most prominent in windows with animated content, such as when you’re playing a video in Windows Media Player (WMP). But it’s not just about looks. Windows Aero is simply more reliable than the other user experiences. To understand why that’s so, you need to examine Aero’s strict hardware and software requirements.
Source of information : Wiley Windows Vista Secrets SP1 Edition
Subscribe to:
Comments (Atom)
Cloud storage is for blocks too, not just files
One of the misconceptions about cloud storage is that it is only useful for storing files. This assumption comes from the popularity of file...
-
Many of the virus, adware, security, and crash problems with Windows occu when someone installs a driver of dubious origin. The driver suppo...
-
A breakthrough in virtual tape technology came when dedupe technology was integrated with VTLs. Like previous-generation VTLs, dedupe VTLs r...
-
The Berkeley motes are a family of embedded sensor nodes sharing roughly the same architecture. Let us take the MICA mote as an example. T...

